Kind time of the day, dear friends. I got a little sick here, on March 8th and spent the whole weekend with a fever, finding strength only to respond to your comments. Today in the evening it was a little let up and I decided that I needed to write something, and to lie on the couch, even with a laptop I was already tired of it :).
Judging by the popularity of the articles on this site, on solving problems with Wi-Fi and on setting up Wi-Fi routers, we can say with confidence that now there is such a massive Wi-Fi installation equipment. And this is not strange, because everyone wants to have a devil wired Internet- it is comfortable and modern.
But just buying a router is not enough, you still need to connect it, configure it, then connect devices to it. And here, as a rule, there are a lot of problems, mistakes and questions that we are trying to solve.
Something carried me in the wrong direction, now I'll start writing about the meaning of life :). Today I want to tell you how to connect to Wi-Fi with a hidden network name (SSID). Perhaps you have already read the article, if you have not read it, then be sure to read it. In one of the paragraphs I wrote that very good way to protect home wifi network, this is to hide the network name (SSID). That is, your network will not appear in the list of available for connection. And you can connect to it only by entering the name of the network, and of course the password.I think you know how to connect to a regular Wi-Fi network, although judging by the comments that I met on the blog, not everyone knows how to do this. What is the difference between connecting to a network with a public name (SSID) and with a hidden name? Just when you turn on Wi-Fi and look at the list available networks, then you will not see a network with a hidden SSID there, and this does not mean that it does not work. This is such a protection, and very effective.
We connect to a Wi-Fi network with a hidden name (SSID)
Right-click on the Internet connection status icon on the notification bar and select.

On the left, select the item.

Click on the "Add" button and in the window that opens, select "Create a network profile manually".


In the next window, click the "Close" button.
If you entered everything correctly, then a network connection should occur. The connection we created will appear in the list of wireless networks. It can also be changed or deleted there.

Here is such an instruction, friends, I think that it will come in handy for you. You will need to write more small articles on how to connect to a regular Wi-Fi network and how to create a computer-to-computer connection via Wi-Fi. Good luck!
More on the site:
How to connect to Wi-Fi with hidden network name (SSID)? updated: March 10, 2013 by the author: admin
To transfer data in local and global networks, the sending device must know the address of the receiving device. Therefore, each networked computer has a unique address, and not one, but three addresses: physical or hardwarenetwork(IP address); symbolic(common computer name or fully qualified domain name).
The physical address of the computer
The physical (hardware) address of a computer depends on the technology with which the network is built. On Ethernet networks, this is the network adapter. The MAC address is hardcoded into a network card by its manufacturer and is usually written in 12 hexadecimal digits (for example, 00-03-BC-12-5D-4E). This is a guaranteed unique address: the first six characters identify the manufacturing company, which makes sure that the remaining six characters are not repeated on the production line. The MAC address is selected by the manufacturer of the network equipment from the address space allocated for it under the license. When the car is replaced network adapter, then its MAC address also changes.
Find out the MAC address of the network card your computer as follows:
1. Go to "Start" - "Run" - enter the command from the keyboard cmd- "OK".
2. Enter the command ipconfig / all and press the Enter key.
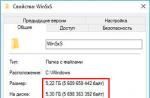
This command allows you to get full information about all network cards of the PC. Therefore, find in this window the line Physical adress- it will indicate your network card. In my case, it looks like this: 
Computer network address
Network address, or IP address used in TCP / IP networks when exchanging data at the network level. IP stands for Internet Protocol- Internet protocol. A computer's IP address is 32 bits long and has four parts called octets. Each octet can range from 0 to 255 (for example, 90.188.125.200). Octets are separated from each other by dots.
The IP address of the computer, for example 192.168.1.10
, consists of two parts - the network number (sometimes called network identifier
) and network computer numbers (host id
). The network number must be the same for all computers on the network, and in our example, the network number will be 192.168.1
... The computer number must be unique on this network, and the computer in our example has the number 10
.
The IP addresses of computers on different networks can have the same numbers. For example computers with IP addresses 192.168.1.10
and 192.168.15.10
although they have the same numbers ( 10
), but belong to different networks ( 1
and 15
). Since the addresses of the networks are different, computers cannot be confused with each other.
The IP addresses of computers on the same network should not be repeated. For example, it is unacceptable to use your local network the same addresses 192.168.1.20 and 192.168.1.20. This will lead to their conflict. If you turn on one of these computers earlier, then when you turn on the second computer, you will see an error message about the IP address:  In this case, just change the address on one of the computers.
In this case, just change the address on one of the computers.
To separate the network number from the computer number, apply Subnet mask... Superficially, the subnet mask is the same set of four octets separated by dots. But, as a rule, most of the numbers in it are 255
and 0
.
255
indicates the bits intended for the network address in other places (which correspond to the value 0
) must be the address of the computer. The lower the mask value, the more computers are connected to this subnet. The network mask is assigned to the computer at the same time as the IP address. To make it clear, let's give a simple example: a network 192.168.0.0
with mask 255.255.255.0
may contain computers with addresses from 192.168.0.1
before 192.168.0.254
... And the network 192.168.0.0
with mask 255.255.255.128
allows addresses from 192.168.0.1
before 192.168.0.127
.
Networks with big amount computers are usually divided into parts called subnets
... Subnetting is used to provide increased security and differentiate access to resources on different subnets. Computers of different subnets will not be able to transmit packets to each other without a special device - a router, and, therefore, no one will be able to penetrate into a subnet protected in this way. To create subnets, some of the space in the IP address reserved for the host number is allocated to the subnet numbers.
Let's consider an example, when we have 50 computers in the local network and it is required to configure them so that 20 computers can “communicate” with each other, but cannot transmit and receive data from the other 10 computers, which must also communicate only with each other. The solution to this problem is quite simple - we divide our network into two subnets... In the first subnet we “distribute” to computers (we have 20 of them) numbers from the range 192.168.1.1
– 192.168.1.20
, and in the second subnet for the remaining 10 computers we distribute numbers from the range 192.168.2.1
– 192.168.2.10
.
If your computer is connected to a local network or the Internet, you can find out its IP address and subnet mask in a way we already know:
1. Go to "Start" - "Run" - type cmd and click “OK”.
2. In the window that opens, enter the command ipconfig / all and press the Enter key.
You will see the IP address of the computer and the subnet mask in the corresponding lines:  The network number can be chosen arbitrarily by the administrator, or assigned on the recommendation of a special unit of the Internet (Network Information Center - NIC), if the network is to work as a part of the Internet. Typically, ISPs obtain address ranges from NIC units and then distribute them to their subscribers. it external IP addresses
(accessible from the Internet), for example 90.188.125.200.
The network number can be chosen arbitrarily by the administrator, or assigned on the recommendation of a special unit of the Internet (Network Information Center - NIC), if the network is to work as a part of the Internet. Typically, ISPs obtain address ranges from NIC units and then distribute them to their subscribers. it external IP addresses
(accessible from the Internet), for example 90.188.125.200.
Reserved for local networks internal IP addresses (they cannot be accessed via the Internet without special software) from the ranges:
- 192.168.0.1 – 192.168.254.254
- 10.0.0.1 – 10.254.254.254
- 172.16.0.1 – 172.31.254.254
From these ranges, you, as a system administrator, will assign addresses to computers on your local network. If you “hard” fix the IP address in the computer settings, then this address will be called static Is the permanent, unchangeable IP address of the PC.
There is also another type of IP addresses - dynamic that change each time the computer logs on to the network. The DHCP service is responsible for managing the dynamic address allocation process. I will tell you about it in one of the following articles.
Network computer name
In addition to physical and network addresses, a computer may also have symbolic address – computer name ... A computer name is a more convenient and human-readable designation for a computer on a network. Distinguish NetBIOS names and fully qualified domain names of computers .
NetBIOS names are used on peer-to-peer LANs, in which computers are organized into working groups ... NetBIOS is a protocol for the interaction of programs over a computer network. NetBIOS recognizes common literal computer names and is responsible for transferring data between them. Windows explorer for viewing the local network, it provides the Network Neighborhood folder, which automatically displays the NetBIOS names of computers on your local network.
The NetBIOS name can be up to 15 characters long and must be in English.
To find out the NetBIOS name of your computer do the following:
1. Right click on the “My Computer” icon on the desktop - select “Properties”.
2. Click the “Computer Name” tab.
3. Click the "Change" button - then "Advanced".
4. Find the line “NetBIOS computer name”. Below is the name of your PC:  5. Click the “Cancel” button. In the "Change computer name" window, you can change the NetBIOS name in the "Computer name" field:
5. Click the “Cancel” button. In the "Change computer name" window, you can change the NetBIOS name in the "Computer name" field:  Large hierarchical domain-based networks use fully qualified domain names
computers, for example webserver.ibm.com... The domain name of a computer consists of three parts, where the first part is the hostname ( webserver), the second is the company's domain name ( ibm), and the last is the domain name of the country (for example, ru - Russia) or the name of one of the special domains that indicate the organization's domain belongs to one of the activity profiles ( com, gov, edu).
Large hierarchical domain-based networks use fully qualified domain names
computers, for example webserver.ibm.com... The domain name of a computer consists of three parts, where the first part is the hostname ( webserver), the second is the company's domain name ( ibm), and the last is the domain name of the country (for example, ru - Russia) or the name of one of the special domains that indicate the organization's domain belongs to one of the activity profiles ( com, gov, edu).
Names in local computer networks are assigned to workgroups, computers and network resources. The name of the computer and the workgroup in which the computer will be taken into account is given by the network administrator (the person responsible for organizing the work of the local computer network) when the PC is connected to the network and the Windows OS is installed on it in the network version. After that, a PC connected to the local network becomes visible in other nodes of this network as part of a workgroup with the name specified by the network administrator, into which he enters under his unique name (also set by the network administrator).
Network resources also have names. When a network administrator or computer owner provides a computer resource for sharing on the network, it gives this resource a network name (using the appropriate Windows OS tools on the PC). The resource will be visible on the network with this name, which allows other users to use this resource.
On the net under Windows control to indicate files on network computers, the Uniform Naming Convention (UNC) is used, which expands the concept of a full file name discussed earlier, supplementing it with the name of a computer on the network. For example, the UNC format for specifying the F1 file located on a network computer named COMPUTER on device C: in a folder named P1 looks like this:
\\ COMPUTER \ S: \ P1 \ F1
The Windows graphical user interface virtually eliminates the need to use UNC names for the network user. To gain access to any resource, you just need to double-click on its icon, previously using the mouse to open the required workgroup and required computer.
Controlling access to network resources
Sharing network resources such as files may cause them to be unintentionally distorted or even destroyed. Therefore, not all the resources of another computer may be available for network use or access to resources may be restricted. The network administrator or the owner of the computer has the ability to set access rights from the network to the resources of his computer. Only those resources that the network administrator or the owner of the computer declares to be available for public use will be visible on the network. All such announcements are made using graphical user interface (GUI) tools that allow you to manipulate object properties.
The following access rights to the resource can be set on the network:
If for any reason there is a need to increase access rights, then you need to contact the owner of the computer or the network administrator.
Control questions
1. What are the reasons for the creation of computer networks?
2. What is needed to create a computer network?
3. What is called a protocol in computer networks?
4. What is fundamentally different network hardware local and global computer networks?
5. What are called gateways in computer networks?
6. What is included in the concept of a network resource? Controlling access to a network resource.
7. How are working groups created in a computer network, what role do they play?
8. Name of computers in the network and access to a remote resource.
Global internet
Global networks
An organization that has decided to integrate its computers into a local computer network, it is enough to purchase its own network equipment and network software to ensure communication between computers . It is a different matter when computers are located at a considerable distance from each other, for example, in different cities. Communication between computers located at great distances from each other is called computer telecommunications and is carried out in a fundamentally different way. The creation and maintenance of computer telecommunications requires incomparably greater material costs than the creation of local computer networks and is within the power of only specialized organizations operating in the communication services market. Computer networks that use telecommunication means of communication to transfer information between computers are called global networks.
Currently, there is a wide range of different telecommunication means of communication, which differ in the speed of information transmission and in the cost of communication services. The slowest are telephone lines, as they were not originally intended for organizing communication between computers, but only for telephone conversations, but they are the cheapest and are available in almost all organizations, institutions and in many homes. A device for organizing computer communication over telephone lines appeared in the early 70s and was named modem ( mo modulator- dem modulator)... The modem connects to the computer and to the usual telephone socket... The main functions of the modem are to convert the binary code coming from the computer during data transmission into an electrical signal transmitted over the telephone line, and when receiving data, on the contrary, convert the electrical signal received through the telephone line into the corresponding binary code entering the computer. In addition, the modem, on command from the computer, dials the specified telephone number and establishes communication with the modem of another computer.
The main characteristic of a modem is its bandwidth or data transfer rate, measured in bps (bit / sec)... Modems with baud rates up to 33600 bps are widely used today.
Since when typing phone number connection (switching) of communication lines occurs on the automatic telephone exchange (automatic telephone exchange), the telephone lines are called dial-up lines... With the help of dial-up lines, communication between computers is established only for a certain time, during which the exchange of information between computers is possible. In addition to dial-up lines, so-called dedicated lines (channels) of communication, which connect computers constantly. Dedicated channels can be created by laying communication cables or by means of radio communication, and can also be created by permanent commutation of dial-up lines at the PBX. The use of leased lines is much more expensive than dial-up lines, but it allows you to exchange information at high speeds. Therefore, as a rule, local computer networks of organizations are connected to global networks using dedicated channels.
Internet Basics
The most famous global computer network at the present time is the Internet. The name of the word Internet consists of two English words and stands for "Inter - a prefix that means interaction, mutual direction" and "Net - a computer network". In 1999, the Internet connected about 60 million computers and more than 270 million users. We can safely say that the Internet has carried out an information revolution. On the basis of the achievements of this revolution, new technologies of the coming century will be built. The Internet is a worldwide information computer network that unites into a single whole many computer networks operating according to uniform rules. The Internet is not a commercial organization and does not belong to anyone. A distinctive feature of the Internet is its high reliability. If some computers and communication lines fail, the network will continue to function. This reliability is ensured by the fact that the Internet does not a single center management. If some communication lines or computers fail, then information can be transmitted through other communication lines, since there are always several ways of transferring information.
The Internet originated in the United States in the late 1980s and early 1990s, completing a period of intense research into the creation of global information networks. At the same time, national networks were created in other countries. Computer networks of different countries began to unite, and in the 90s the Internet appeared in its present form. Now the Internet unites thousands different networks located all over the world. In Russia, the rapid growth in the number of Internet users began in 1996.
At present, almost all global computer networks are connected to the Internet. They connect to Internet gateways (Fig. 22), that is, computers that are simultaneously connected to the Internet and to another network.
Each gateway has information about all other gateways and networks. When information from one network is sent to a user of another network, it is immediately sent to the gateway of the original network, which sends it to the gateway of the user's network, and from there to the recipient.
Internet users connect to the network through computers from special organizations called Internet service providers or providers. The provider has its own gateway to the Internet and, for a fee, connects computer networks or computers of individual users to the Internet through this gateway. The provider has many communication lines for connecting users to itself and high-speed communication channels for accessing the Internet. In reality, the difference between users and Internet service providers is rather arbitrary. Anyone who has connected their computer to the Internet and installed the necessary system programs, can, in principle, already provide Internet connection services to other users.
Computers connected to the Internet are called Internet sites or sites, from the English word site, which translates as a place, location. Provider sites provide users with access to the Internet. There are also nodes specializing in providing information. For example, many firms create their own sites on the Internet, through which they distribute information about their products and services.
Rice. 22. Scheme of building the Internet
Internet addressing
Domain names. DNS service
The Internet connects millions of computers. To organize access to remote computer with whom you want to exchange information, you must uniquely identify the name of the computer on the network. To be able to uniquely address any computer, the Internet uses the so-called domain name system... In the domain system, a hierarchical principle of building a name is adopted, based on the idea of consistently clarifying the location of the computer in global network... The same principle is applied, for example, in ordinary postal addresses, which use a consistent specification of the country, city, street and house. The country is, as it were, the domain of the inhabitants of the Earth living in this country. City is a domain that belongs to a country domain, etc. Similar to the postal service, computer names on the Internet are set according to rules established by a special system called the Domain Name Service or DNS (Domain Name Service).
When a computer connects to the Internet, it is counted on the network as part of a set of nested domains. To identify a computer in the domain, it is assigned its own name, called the host name. As a result, the domain name of the computer will be represented as a string, in which the names of subdomains are located from right to left. The top-level domain is located in the name to the right, and the lower-level domain is located to the left. Domain names are separated from each other by periods. For example, domain name computer.managers.company.ru denotes a computer with a hostname computer included in the domain managers, which in turn is included in the domain company which is part of the top-level domain ru(Fig. 23). Table 1 lists the names of some of the major Internet-registered top-level domains.

 |
Rice. 23 The structure of the domain name of a computer on the Internet
Although Internet users use symbolic names, computers connected to the network use digital counterparts of domain names called IP addresses to communicate. An IP address is made up of four integers, each of which does not exceed 256, separated by dots. The IP address might look something like this: 193.46.21.13 or 201.8.62.157 .
Domain names and their corresponding IP addresses are stored on the Internet on DNS servers in the form of a large distributed database, which is located on the computers of each Internet provider. When a user tries to connect to any Internet resource, the client computer sends the DNS server the domain name of the computer that the client wants to contact. The DNS server obtains the domain name of the computer, then looks through its database and returns the corresponding IP address and routing information. If this information is absent in its database, it sends a request to the DNS server of a higher domain.
If we recall the days of the birth of the Internet, then a picture involuntarily pops up in my head, where ancient huge computers, wrapped in a bunch of wires, are on the table. But in a modern apartment at the moment everything is different. Huge computers have been replaced by the most compact devices (laptops, smartphones, etc.), cables have become fewer, and in some places they are not at all.
All this became possible thanks to the development of wireless data transmission technologies. Large modems have been replaced with universal ones wifi routers... They are capable of transmitting the wired Internet over a radio frequency network that has its specific name ssid.
Many users, when faced with this for the first time, ask one question: "What is it and what is it for?" First of all, ssid makes the wifi network unique among others, which makes it easier to find and connect. Also, at some points, the name is needed to configure new equipment (router).
This article details the ways to help users find out the ssid of a wireless network.
The first step is to make sure that your computer has an adapter that allows you to connect to the wireless internet. Even if it is known in advance that it is there (for example, in the hands of a laptop), it will be a good form to find out whether it is turned on or not.
There are two ways to do this in Windows:
After making sure that wireless adapter network is on and on, the next step will be to view all existing ssid in the area from the computer. To do this, left-click on the wi-fi icon, which is located at the bottom left side next to the clock. After that, a list should appear with the names of all available points to which you can connect. 
Internal means of Android devices recognition
Now everyone has a gadget in their pocket on the Android platform. Almost all of these devices have communication modules that can connect to a wireless network.
To find out the name of the connection, you need to: go to the main menu, find the "Settings" icon, then go to the Wi-Fi item. Here, in the window that appears, you need to enable the adapter, at the top you can see the corresponding switch. After switching on, after a few seconds, all points that have a name and which can be connected should be displayed. 
Ways for advanced users
To find out more detailed information about the wireless network, many users use specialized programs called sniffers. These are utilities that allow you to determine the name of the network, find hidden ssid, show the mac address of the router and much more.
There are many different sniffers on the network, both paid and free versions... Within the framework of the article, a separate utility will not be described, the general mechanism of the program will be described.
Each sniffer works according to the same algorithm, the only difference is in the calculation procedures and the presence additional functions... First, you need to scan the workspace to find hidden networks, collect ssid information, and other data. 
Then the utility, based on the collected data, shows the user a list of found access points, where information is collected opposite each one: name, signal strength, encryption algorithm, communication channel and much more. Basically, this data is of interest to network engineers who are engaged in network analysis. As a rule, at this stage, the user only needs to know the name, level and operating mode of the required router.
As you can see above, there are many ways to find out the ssid of a wireless network. Many of the methods are very simple and even an inexperienced computer user can handle them. For people who like to discover something new, it is advisable to use a specialized utility - a sniffer. It will allow you to find out not only the name of the network, but also many other useful information, on the basis of which you can optimize the operation of your router as much as possible.
In contact with
With the advent of wireless technologies for creating and connecting to virtual networks, many users have come across the concept of a network SSID. Not everyone knows what this is. Meanwhile, there is nothing difficult in understanding this term. Below we will consider what the SSID of the WiFi network is, and also show how you can find out this parameter and change it.
Network SSID: What is it?
So, from the point of view of computer technology, each wireless network should be detected when trying to connect by some in a simple way... For this, the concept of the network SSID parameter was introduced. What is this? In its broadest sense, SSID is a unique identifier for a network that distinguishes it from all others, in other words, the name or name of the VPN.
Thus, the user, when trying to search for a network and connect to it, does not need to rummage through some digital data or to determine a possible access point. It is enough to know the network name (SSID) and the password to access it.
What is WiFi SSID and how to change this setting
Typically, the value of the network identifier (name) is set initially when creating a wireless connection. Basic settings are made to By default, this can be the model number or the brand of equipment, however, for the convenience of defining the network, its own name is set.

This is done in the settings section of the router, which is responsible for the wireless connection. To set a name or change it, just find an item like Wireless Network Name or SSID, where the desired name is indicated. If the user wants to avoid security problems, it is best not to use some personal data for this setting, which may draw unnecessary attention.
Viewers for available networks
Now networks. To do this, with the Wi-Fi adapter turned on, you should pay attention to the wireless connection icon in the system tray.

Left-clicking on it brings up a pop-up window in which all available networks will be displayed.

To check the network activity, use the ncpa.cpl command, which is entered in the Run console, and then look at the connection status. If it is inactive, you need to select the enable option from the right-click menu. You can also see all connections in the network management section, where you select the item for changing adapter properties. The Wi-Fi module is turned on either by special buttons on the laptop panel, or by combining the Fn key with something else (usually these are the F1-F12 function buttons, but there may be exceptions).

WITH mobile devices and even easier. It is enough to turn on the connection, and then select the desired network from the list, and then enter the access password, if any.
An advanced user can extract more information using sniffers. With their help, you can view the MAC address of the router, see hidden networks, find out information about the communication channel, signal level, the number of connected subscribers at the current moment, etc.
How to hide the SSID of the network?
In connection with the above, let's look at one more situation in relation to the SSID of the network. It is already clear what this is. Now a few words about how you can hide the network name so that it does not appear in the list of available connections.

The easiest way to do this is where you need to find a special item with a string to hide the SSID (Hide SSID or something like that). If in the future you need to connect to a hidden network, you should create a new connection in the control section wireless networks and create a profile manually. After that, you will need to enter the SSID of the network, set the types of security and encryption, and also use the security key (password) that were specified in the router settings at the initial stage of creating a connection or when changing the settings.
Multi-SSID
In principle, for any connection, you can create several access points with your own names and parameters. The essence of this process is that in this way you can split the connection speed among several user groups. For example, such settings will be relevant if one network is required for the personal use of the head of the enterprise, the second for personnel, and the third for public access.

These parameters can be set on the same router, but use the corresponding Multi-SSID section for this, where the point names, passwords and many other parameters are set.
Conclusion
It remains to add that, in general, there is nothing difficult in understanding the definition of SSIDs of networks. The accompanying parameters and additional settings are another matter. But it is unlikely that an ordinary user will do such things. Usually, knowledge in this area is required more by system administrators or employees of ISPs that provide Internet access services.