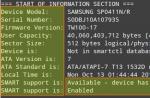
If you do not allocate the budget, and there are problems, it remains to be patient and coffee and. In the transmission networks, this at the speeds of 1 Gbit / s and above the traffic grip buffer is filled instantly and a sufficiently large data array is obtained at the output. This data array, understanding the interaction between different network devices can be filtered by different parameters. For this, Wireshark has several possibilities:
Color encoding of erroneous packets - can be configured for yourself. Packages that carry a mistake will be highlighted in a special color buffer.
Filter through the filtering string. You have extensive experience in working with Wireshark and protocols and can enter the filter yourself. A large selection of filters can be found.
Allocation of any area in the package, the right click of the mouse and "apply as a filter". Method for beginners: Very convenient, because you do not need to break your head.

What basic filters exist to display traffic?
Wireshark protocol filter
Enough in the filter string, enter the name of the protocol and press the input. The screen will remain packets that refer to the desired protocol. Thus, the filter looks like:

If the capture buffer needs to be filtering over several protocols, then you need to list all the desired protocols and divide them with sign ||. For example:
aRP || http || icmp

Wireshark IP address filter and MAC filter
Depending on the direction of traffic, the filter will be slightly different. For example, we want to filter by the IP address of the sender 50.116.24.50:
ip.src \u003d\u003d 10.0.10.163

By the recipient, the filter will look like IP.dst \u003d\u003d X.x.x.x.x, and if we want to see packages regardless of the direction of traffic, then it is enough to enter:
ip.addr \u003d\u003d 50.116.24.50
If we need to exclude some address from the selection field, then you need to add! \u003d. Example:
iP.SRC! \u003d 80.68.246.17
If we analyze traffic inside the local network and know the Mac address of the user, then you can specify your MAC address as the Wireshark filter, for example:
eth.addr \u003d\u003d AA: BB: CC: DD: EE: FF
Wireshark filter by port number
When analyzing traffic, we can configure the filter by the port number on which the traffic transmission is a protocol. Rooms of all registered ports can be recognized as an example:
As well as with IP and MAS addresses, we can separately filter by ports of receipt or departure tCP.. srcport. and tCP.. dSTport.. In addition to specifying the Wireshark port numbers, it gives an excellent opportunity to filter the flag buffer in the TCP protocol. For example, if we want to see TCP packets with the SYN flag (establishing a connection between devices), then enter the search bar:

Popular filters
The table below shows the most popular filters for displaying the contents of the capture buffer:
|
Filter for display |
Description |
Example of writing |
|
MAC address of the sender or recipient |
eth.addr \u003d\u003d 00: 1A: 6B: CE: FC: BB |
|
|
MAC address of the Apiary |
eth.src \u003d\u003d 00: 1A: 6B: CE: FC: BB |
|
|
MAC address of the recipient |
eth.dst \u003d\u003d 00: 1A: 6B: CE: FC: BB |
|
|
ARP Protocol - MAC Recipient Address |
arp.dst.hw_mac \u003d\u003d 00: 1A: 6B: CE: FC: BB |
|
|
aRP.DST.PROTO_IPV4. |
ARP protocol - IP address version 4 recipient |
arp.dst.proto_ipv4 \u003d\u003d 10/10/10 |
|
ARP protocol - MAC sender address |
arp.src.hw_mac \u003d\u003d 00: 1A: 6B: CE: FC: BB |
|
|
aRP.SRC.PROTO_IPV4. |
ARP protocol - IP address version 4 sender |
arp.src.proto_ipv4 \u003d\u003d 10/10/10 |
|
VLAN identifier |
||
|
IP address version 4 recipient or sender |
ip.addr \u003d\u003d 10/10/10 |
|
|
IP address version 4 recipient |
ip.addr \u003d\u003d 10/10/10 |
|
|
IP address version 4 sender |
ip.src \u003d\u003d 10/10/10 |
|
|
IP Protocol (Decimal) |
||
|
IP address version 6 recipient or sender |
ipv6.addr \u003d\u003d 2001 :: 5 |
|
|
IP address version 6 sender |
ipv6.addr \u003d\u003d 2001 :: 5 |
|
|
IP address version 6 recipient |
ipv6.dst \u003d\u003d 2001 :: 5 |
|
|
TCP Port Recipient or Sender |
||
|
TCP Port Recipient |
tCP.DSTPORT \u003d\u003d 80. |
|
|
TCP port of the sender |
tCP.Srcport \u003d\u003d 60234. |
|
|
UDP Port Recipient or Sender |
||
|
UDP Port Recipient |
udp.dstport \u003d\u003d 513. |
|
|
UDP port of the sender |
uDP.Srcport \u003d\u003d 40000. |
|
|
vtp.vlan_info.vlan_name. |
vtp.vlan_info.vlan_name \u003d\u003d Test |
|
|
bgp.originator_id |
BGP identifier (IPv4 address) |
bgp.originator_id \u003d\u003d 192.168.10.15 |
|
Next Hop BGP (IPv4 address) |
bGP.NEXT_HOP \u003d\u003d 192.168.10.15 |
|
|
RIP IPv4 Address |
rip.ip \u003d\u003d 200.0.2.0 |
|
|
OSPF router identifier |
ospf.advrouter \u003d\u003d 192.168.170.8. |
|
|
EIGRP autonomous system number |
||
|
Virtual IP address on the HSRP protocol |
hsrp.virt_ip \u003d\u003d 192.168.23.250 |
|
|
Virtual IP address by VRRP Protocol |
vrrp.ip_addr \u003d\u003d 192.168.23.250 |
|
|
Mac address sender or recipient Wi-Fi |
wLAN.ADDR \u003d\u003d 00: 1A: 6B: CE: FC: BB |
|
|
MAC address of the Wi-Fi Apiary |
wLAN.SA \u003d\u003d 00: 1A: 6B: CE: FC: BB |
|
|
MAC address of the recipient Wi-Fi |
wLAN.DA \u003d\u003d 00: 1A: 6B: CE: FC: BB |
And what filters most often use in your work?
Introduction
When studying network interactions at the level of individual packages, datagrams, segments and applied level messages, it is often necessary to solve traffic filtering tasks. The essence of the use of filters is to search for both groups, as well as individual transmission units of interest for further analysis. This functionality is extremely useful in tools intended for interception and studying network traffic (sniffers), and helps the system administrator or information security specialist to find a product of useful information in intensive information flows of modern networks.
The open multi-platform present in this article has two filter subsystems in its composition: traffic interception time (Capture Filters) and Display Filters. As you know, the first subsystem is based on the Pacpet Capture Rules Language. The "cleaning" of traffic during its collection, in particular, reduces the number of assigned packets, thereby keeping the place in memory or on the hard disk. As for the display filters, they, being the built-in Wireshark function, are intended for "customization" in the graphical interface of the program already intercepted traffic.
About the languages \u200b\u200bof filters
The ability to intercept traffic for monitoring and debug purposes is present in the network stack of any operating system. It is carried out using the so-called batch filter (Packet Filter), which is part of the system kernel and receiving received / sent packets from the network card driver. The most famous batch filters for UNIX-like OS are BPF (Berkeley Packet Filter) and LSF (Linux Socket Filter).
So, the sample of traffic on the specified criteria in Bpf. Implemented as a special register-oriented primitive machine language, the interpreter for which actually acts as a batch filter. Programs in this language can extract fragments from packets, compare the data obtained with specified values, check individual bits, perform arithmetic operations, and then take or drop packages depending on the results of all these tests. "Low-level" approach is useful for programmers developing libraries of network functions and various utilities.
Simple users usually use the "high-level" languages \u200b\u200bof filters. A typical application language used in a sniffer for descriptions of traffic rules allows you to design expression primitives based on separate messaging fields of various protocols. At the same time, as a criterion, the ratio of the field value to a certain value (equal, greater, less), the coincidence of the value with the template, or simply the presence of the field in the message. Primitives can be combined into a complex expression using logical functions ("and", "or", "not", etc.).
In the world of open software in fact, the syntax used in the PCAP library is actually standard. It is the basis not only for Wireshark, but also for other open source utilities, such as, for example, the well-known UNIX Console Sniffer Tcpdump. Actually, PCAP and TCPDUMP are a joint project. The popular SNORT intrusion detection system in packet interception mode is also used PCAP format to determine the traffic filtering rules.
Basics of PCAP filters
So, the filter includes one or more primitives. . The primitive usually consists of an object (number or name) and one or more specifiers defining the protocol (Ether, FDDI, TR, WLAN, IP, IP6, ARP, RARP, DECNET, TCP, UDP), direction (SRC, DST, ANY and etc.) and the type of object (Host, Net, Port, etc.). For example, to intercept the packets in which the outgoing IP address is 192.168.56.102, you should use a form filter:
IP SRC HOST 192.168.56.102
Or to record the traffic of the ARP protocol, in which network nodes 192.168.56.0 participate:
ARP NET 192.168.56
Frequently used specifiers are reduced to the table (optional components are indicated - alternative - |, objects -< >). The full list can be found in the PCAP documentation (in Linux available in the user manual using the MAN PCAP-FILTER command).
In order to combine several primitives in one expression, logic functions are used: "and" (indicated by keyword and or &&), "or" (or or ||), "not" (not or!). For example, such a design is suitable for intercepting traffic SSH protocol for the node 192.168.56.102:
TCP PORT 22 AND HOST 192.168.56.102
For very complex expressions, you should use brackets. For example:
Net 192.168.56.0/24 and (TCP Port 21 or TCP Port 22)
PCAP filters without restrictions
For those who are used to living according to their own rules, the PCAP library provides random access to the contents of network packets using the entire power of the OS batch filter. This is done with a fairly simple syntax:
Proto [EXP: SIZE]
where, the proto parameter is one of the protocols supported by Wireshark; EXP - offset in bytes, relative to the beginning of the layer specified in Proto, A Size - the number of bytes for the extraction.
Considering the fact that in the primitives it is possible to apply comparison operations in the notation of the programming language C (\u003e, \u003d,
An example, however, has only a methodological meaning, since this protocol is easily filtered by the standard ICMP rule.
But to choose on the fly from the traffic made by the GET method HTTP requests - not such a simple task for PCAP. And the decision proposed in the documentation claims originality:
PORT 80 AND TCP [((TCP & 0xF0) \u003e\u003e 2): 4] \u003d 0x47455420
This filter checks the presence of bytes "G", "E", "T" and "" (hexadecimal values \u200b\u200b47, 45, 54 and 20) immediately after the TCP header, the length of which is calculated by the expression "TCP & 0xF0) \u003e\u003e 2".
As can be seen from the last example, in addition to comparison operations, the user directly in the primitives are also available binary operators C (+, -, *, /, & |,\u003e).
About display filters
If we talk about the differences display filters From PCAP filters, except the format of recording specifiers (protocol fields look like., For example, IP.Len), you can also call additional support for English notation in comparison operations (EQ - equal, GT - more, LT - less, GE - more or Equally, LE is less than or equal to) and binary operators (and, or, xor, not), as well as support for substring.
A selection of substring in the fields is similar to extracting arbitrary bytes from the PCAP filters, however, it has a more flexible syntax. For example, such an expression will check the first 4 bytes field of the source MAC address of the Ethernet frame (equivalent to):
Eth.src [: 4] \u003d\u003d 00: 1d: 72: 01
Of course, the differences in filters will be that PCAP rules are used when intercepting traffic; The graphical interface is configured in the "Capture Options" dialog box (by the way, it is possible to memorize frequently used expressions). And display filters work with packages placed in the list of the main program window:

A functionally built-in Wireshark filtering subsystem is much friendlier to the user. In particular, there is no need to remember the details of the message format (offsets, field size, etc.). The required message field of this protocol can be easily found in the Filter Expression Settings window, as well as select a condition and predetermined value from the list for this field or specify your own. For any of the multitude of protocols supported by Wireshark, in such a simple way, you can configure the display filter.
A very significant will be almost an academic example of determining the moment of overflow of the TCP-segment buffer using the display rule below:
Tcp.window_size \u003d\u003d 0 && tcp.flags.reset! \u003d 1
Conclusion
The Wireshark protocol analyzer has a powerful package filtering system makes it possible to create complex rules using logical functions and binary operators. Interception time filters are standard and will be familiar to users using network utilities based on the PCAP library, such as TCPDUMP. Package display rules are easy to learn and use, thanks to the capabilities of the graphical interface of the program under consideration. In general, the functionality of the Wireshark filtering system allows you to use the benefits of a low-level batch filter quite efficiently.
Introduction
When studying network interactions at the level of individual packages, datagrams, segments and applied level messages, it is often necessary to solve traffic filtering tasks. The essence of the use of filters is to search for both groups, as well as individual transmission units of interest for further analysis. This functionality is extremely useful in tools intended for interception and studying network traffic (sniffers), and helps the system administrator or information security specialist to find a product of useful information in intensive information flows of modern networks.
Open multiplatform considered in this article wireshark Protocol Analyzer It has two filter subsystems: traffic interception time and display filters (Display Filters). As you know, the first subsystem is based on the Pacpet Capture Rules Language. The "cleaning" of traffic during its collection, in particular, reduces the number of assigned packets, thereby keeping the place in memory or on the hard disk. As for the display filters, they, being the built-in Wireshark function, are intended for "customization" in the graphical interface of the program already intercepted traffic.
About the languages \u200b\u200bof filters
The ability to intercept traffic for monitoring and debug purposes is present in the network stack of any operating system. It is carried out using the so-called batch filter (Packet Filter), which is part of the system kernel and receiving received / sent packets from the network card driver. The most famous batch filters for UNIX-like OS are BPF (Berkeley Packet Filter) and LSF (Linux Socket Filter).
So, the sample of traffic on the specified criteria in Bpf. Implemented as a special register-oriented primitive machine language, the interpreter for which actually acts as a batch filter. Programs in this language can extract fragments from packets, compare the data obtained with specified values, check individual bits, perform arithmetic operations, and then take or drop packages depending on the results of all these tests. "Low-level" approach is useful for programmers developing libraries of network functions and various utilities.
Simple users usually use the "high-level" languages \u200b\u200bof filters. A typical application language used in a sniffer for descriptions of traffic rules allows you to design expression primitives based on separate messaging fields of various protocols. At the same time, as a criterion, the ratio of the field value to a certain value (equal, greater, less), the coincidence of the value with the template, or simply the presence of the field in the message. Primitives can be combined into a complex expression using logical functions ("and", "or", "not", etc.).
In the world of open software in fact, the syntax used in the PCAP library is actually standard. It is the basis not only for Wireshark, but also for other open source utilities, such as, for example, the well-known UNIX Console Sniffer Tcpdump. Actually, PCAP and TCPDUMP are a joint project. The popular SNORT intrusion detection system in packet interception mode is also used PCAP format to determine the traffic filtering rules.
Basics of PCAP filters
So, the filter includes one or more primitives. . The primitive usually consists of an object (number or name) and one or more specifiers defining the protocol (Ether, FDDI, TR, WLAN, IP, IP6, ARP, RARP, DECNET, TCP, UDP), direction (SRC, DST, ANY and etc.) and the type of object (Host, Net, Port, etc.). For example, to intercept the packets in which the outgoing IP address is 192.168.56.102, you should use a form filter:
IP SRC HOST 192.168.56.102
Or to record the traffic of the ARP protocol, in which network nodes 192.168.56.0 participate:
ARP NET 192.168.56
Frequently used specifiers are reduced to the table (optional components are indicated - alternative - |, objects -< >). The full list can be found in the PCAP documentation (in Linux available in the user manual using the MAN PCAP-FILTER command).
In order to combine several primitives in one expression, logic functions are used: "and" (indicated by keyword and or &&), "or" (or or ||), "not" (not or!). For example, such a design is suitable for intercepting traffic SSH protocol for the node 192.168.56.102:
TCP PORT 22 AND HOST 192.168.56.102
For very complex expressions, you should use brackets. For example:
Net 192.168.56.0/24 and (TCP Port 21 or TCP Port 22)
PCAP filters without restrictions
For those who are used to living according to their own rules, the PCAP library provides random access to the contents of network packets using the entire power of the OS batch filter. This is done with a fairly simple syntax:
Proto [EXP: SIZE]
where, the proto parameter is one of the protocols supported by Wireshark; EXP - offset in bytes, relative to the beginning of the layer specified in Proto, A Size - the number of bytes for the extraction.
Considering the fact that in the primitives it is possible to apply comparison operations in the notation of the programming language C (\u003e, \u003d,
An example, however, has only a methodological meaning, since this protocol is easily filtered by the standard ICMP rule.
But to choose on the fly from the traffic made by the GET method HTTP requests - not such a simple task for PCAP. And the decision proposed in the documentation claims originality:
PORT 80 AND TCP [((TCP & 0xF0) \u003e\u003e 2): 4] \u003d 0x47455420
This filter checks the presence of bytes "G", "E", "T" and "" (hexadecimal values \u200b\u200b47, 45, 54 and 20) immediately after the TCP header, the length of which is calculated by the expression "TCP & 0xF0) \u003e\u003e 2".
As can be seen from the last example, in addition to comparison operations, the user directly in the primitives are also available binary operators C (+, -, *, /, & |,\u003e).
About display filters
If we talk about the differences display filters From PCAP filters, except the format of recording specifiers (protocol fields look like., For example, IP.Len), you can also call additional support for English notation in comparison operations (EQ - equal, GT - more, LT - less, GE - more or Equally, LE is less than or equal to) and binary operators (and, or, xor, not), as well as support for substring.
A selection of substring in the fields is similar to extracting arbitrary bytes from the PCAP filters, however, it has a more flexible syntax. For example, such an expression will check the first 4 bytes field of the source MAC address of the Ethernet frame (equivalent to):
Eth.src [: 4] \u003d\u003d 00: 1d: 72: 01
Of course, the differences in filters will be that PCAP rules are used when intercepting traffic; The graphical interface is configured in the "Capture Options" dialog box (by the way, it is possible to memorize frequently used expressions). And display filters work with packages placed in the list of the main program window:

A functionally built-in Wireshark filtering subsystem is much friendlier to the user. In particular, there is no need to remember the details of the message format (offsets, field size, etc.). The required message field of this protocol can be easily found in the Filter Expression Settings window, as well as select a condition and predetermined value from the list for this field or specify your own. For any of the multitude of protocols supported by Wireshark, in such a simple way, you can configure the display filter.
A very significant will be almost an academic example of determining the moment of overflow of the TCP-segment buffer using the display rule below:
Tcp.window_size \u003d\u003d 0 && tcp.flags.reset! \u003d 1
Conclusion
The Wireshark protocol analyzer has a powerful package filtering system makes it possible to create complex rules using logical functions and binary operators. Interception time filters are standard and will be familiar to users using network utilities based on the PCAP library, such as TCPDUMP. Package display rules are easy to learn and use, thanks to the capabilities of the graphical interface of the program under consideration. In general, the functionality of the Wireshark filtering system allows you to use the benefits of a low-level batch filter quite efficiently.
Wireshark: How to use?
Hello, friends! In this article I will try to explain and tell you about the very necessary what you need to know when using Wireshark on LinuxAnd I will show the analysis of three types of network traffic. This manual is applicable for Wireshark under Windows.
If you are a beginner in information security, and quite well understand what a sniffer (traffic analyzer) is, I advise you to read the article, and only then read this article about how to use Wireshark.
Very popular and extremely skillful network Protocol Analyzerwho developed Gerald Combs, Wireshark appeared in June 2006, when the CommBS renamed the Ethereal network tool, also created by him, because it changed the work and could not use the old name anymore. Today, most use Wireshark, and Ethereal has become a story.
Wireshark: Best Sniffer
You may ask than Wireshark differs from other network analyzers - except that it is free - and why don't we just start promoting the use of TCPDUMP to capture packages?
The main advantage of Wireshark is that this is a graphic application. Data collection and checking network traffic in the user interface is a very comfortable thing, as it allows you to deal with complex network data.
How to use Wireshark?
To begin the newcomer to deal with Wireshark, he needs to understand the network traffic. In this case, the purpose of this article is to clarify you the foundations of TCP / IP so that you can make the necessary conclusions on network traffic that is analyzed.
 TCP package format and IP package.
TCP package format and IP package. If you run Wireshark on behalf of a regular user, you will not be able to use network interfaces for data collection due to the default file permissions available in the network interfaces. It is convenient to run Wireshark on behalf of Root (Sudo Wireshark) when collecting data and on behalf of a regular user-to analyze data.
Alternatively, you can collect network data using the TCPDUMP command line utility on behalf of ROOT and then analyze them using Wireshark. Please do not forget that data collection using Wireshark in a strongly downloaded network can slow down the computer, or, even worse, do not allow you to collect the necessary data, because Wireshark requires more system resources than the command line program. In such cases, the most reasonable solution for collecting data on network traffic will be using TCPDUMP.
Capture network data using Wireshark
The simplest way to start capturing network packet data is to select after the Wireshark launch the interface you need and click on Start. Wireshark will show network data on your screen depending on your network traffic. Please note: you can choose more than one interface. If you do not know anything about TCP, IP or other protocols, the result may seem difficult to read and understand.
To stop the data capture process, select Capture\u003e Stop in the menu. Alternatively, you can click on the fourth icon on the left, with a red square (this is a reduction from "stop capturing Live data") in the Main toolbar (Note, its exact location depends on your version of Wireshark). You can only press this button in the process of collecting network data.
When using the described data capture method, you cannot change the default Capture options configured in Wireshark [Capture Options]. You can see and change the Capture Options by selecting in the Capture\u003e options menu. Here you can select an interface (s) of the network, to view your IP address, apply data collection filters, translate your network card to the reception mode of all network packets and save the collected data into one or more files. You can even be tiered to stop capturing packets to achieve a specific number of network packets, or a certain time, or a specific amount of data (in bytes).
By default, Wireshark does not save the data collected, but you can always save them later. It is believed that it is best to preserve first, and then study network packets, if only you do not have any particular reasons to do otherwise.
Wireshark allows you to read and analyze already collected network data from a large number of file formats, including TCPDUMP, LIBPCAP, SNOOP from Sun, Nettl from HP, K12 text files, etc. In short, using Wireshark, you can read almost any format of the collected network data. Similarly, Wireshark allows you to save the collected data in different formats. You can even use Wireshark to convep the file from one format to another.
You can also export an existing file as a simple text file from the File menu. This option is mainly designed to handle network data or input them to another program.
Printing option is provided for your packages. In real life, I never used it, but in educational purposes it is very useful to print packets and their full content.
Wireshark display filters
If capture filters are used during network data capture, Wireshark does not take into account network traffic that does not correspond to the filter; while display filters are applied after capturing the data and "hide" network traffic without removing it. You can always disable Display Filter and return your hidden data.
In principle, display filters are considered more useful and versatile than data collection filters, because you are unlikely to know in advance what information you will collect or decide to study. However, the use of filters when capturing the data saves your time and place on the disk, which is the main reason for their application.
Wireshark highlights a syntactically correct filter with a light green background. If the syntax contains errors, the background povels.
Display filters Support comparison operators and logical operators. Display filter http.response.code.
 Three Packages (SYN, SYN + ACK and ASK) TCP Connection Type
Three Packages (SYN, SYN + ACK and ASK) TCP Connection Type 404 && IP.addr \u003d\u003d 192.168.1.1 shows traffic that either comes from IP addresses 192.168.1.1, or goes to IP address 192.168.1.1, which also has a response code 404 (not found) HTTP. Filter! Booo1R &&! IP &&! Agr excludes from the result of Bootp, IP and ARP traffic. Filter Eth.addr \u003d\u003d 01: 23: 45: 67: 89: AB && TCP.PORT \u003d\u003d 25 Displays traffic running from or to a network device with a MAC address 01: 23: 45: 67: 89: Oh, which uses In incoming and outgoing connections, the TCP port for number 25.
Remember that display filters do not solve problems magical way. With proper use, these are exceptionally useful tools, but you still have to interpret the results, find the problem and think about the right solution.
Continuing the article on the next page. To go to the next page, press the 2 button that is under the buttons of social networks.
- availability of a built-in expert system, which will quickly disassemble the buffer for services or error types. What will significantly speed up the localization time of the problem and work with an already sorted and previously estimated for you. Here you can pay attention to solutions from Viavi Solutions called OBServer or on the Clearsight Analyzer from NetScout.If you do not allocate the budget, and there are problems, it remains to be patient and coffee and. In the transmission networks, this at the speeds of 1 Gbit / s and above the traffic grip buffer is filled instantly and a sufficiently large data array is obtained at the output. This data array, understanding the interaction between different network devices can be filtered by different parameters. For this, Wireshark has several possibilities:
Color encoding of erroneous packets - can be configured for yourself. Packages that carry a mistake will be highlighted in a special color buffer.
Filter through the filtering string. You have extensive experience in working with Wireshark and protocols and can enter the filter yourself. A large selection of filters can be found.
Allocation of any area in the package, the right click of the mouse and "apply as a filter". Method for beginners: Very convenient, because you do not need to break your head.

What basic filters exist to display traffic?
Wireshark protocol filter
Enough in the filter string, enter the name of the protocol and press the input. The screen will remain packets that refer to the desired protocol. Thus, the filter looks like:

If the capture buffer needs to be filtering over several protocols, then you need to list all the desired protocols and divide them with sign ||. For example:
aRP || http || icmp

Wireshark IP address filter and MAC filter
Depending on the direction of traffic, the filter will be slightly different. For example, we want to filter by the IP address of the sender 50.116.24.50:
ip.src \u003d\u003d 10.0.10.163

By the recipient, the filter will look like IP.dst \u003d\u003d X.x.x.x.x, and if we want to see packages regardless of the direction of traffic, then it is enough to enter:
ip.addr \u003d\u003d 50.116.24.50
If we need to exclude some address from the selection field, then you need to add! \u003d. Example:
iP.SRC! \u003d 80.68.246.17
If we analyze traffic inside the local network and know the Mac address of the user, then you can specify your MAC address as the Wireshark filter, for example:
eth.addr \u003d\u003d AA: BB: CC: DD: EE: FF
Wireshark filter by port number
When analyzing traffic, we can configure the filter by the port number on which the traffic transmission is a protocol. Rooms of all registered ports can be recognized as an example:
As well as with IP and MAS addresses, we can separately filter by ports of receipt or departure tCP.. srcport. and tCP.. dSTport.. In addition to specifying the Wireshark port numbers, it gives an excellent opportunity to filter the flag buffer in the TCP protocol. For example, if we want to see TCP packets with the SYN flag (establishing a connection between devices), then enter the search bar:

Popular filters
The table below shows the most popular filters for displaying the contents of the capture buffer:
|
Filter for display |
Description |
Example of writing |
|
MAC address of the sender or recipient |
eth.addr \u003d\u003d 00: 1A: 6B: CE: FC: BB |
|
|
MAC address of the Apiary |
eth.src \u003d\u003d 00: 1A: 6B: CE: FC: BB |
|
|
MAC address of the recipient |
eth.dst \u003d\u003d 00: 1A: 6B: CE: FC: BB |
|
|
ARP Protocol - MAC Recipient Address |
arp.dst.hw_mac \u003d\u003d 00: 1A: 6B: CE: FC: BB |
|
|
aRP.DST.PROTO_IPV4. |
ARP protocol - IP address version 4 recipient |
arp.dst.proto_ipv4 \u003d\u003d 10/10/10 |
|
ARP protocol - MAC sender address |
arp.src.hw_mac \u003d\u003d 00: 1A: 6B: CE: FC: BB |
|
|
aRP.SRC.PROTO_IPV4. |
ARP protocol - IP address version 4 sender |
arp.src.proto_ipv4 \u003d\u003d 10/10/10 |
|
VLAN identifier |
||
|
IP address version 4 recipient or sender |
ip.addr \u003d\u003d 10/10/10 |
|
|
IP address version 4 recipient |
ip.addr \u003d\u003d 10/10/10 |
|
|
IP address version 4 sender |
ip.src \u003d\u003d 10/10/10 |
|
|
IP Protocol (Decimal) |
||
|
IP address version 6 recipient or sender |
ipv6.addr \u003d\u003d 2001 :: 5 |
|
|
IP address version 6 sender |
ipv6.addr \u003d\u003d 2001 :: 5 |
|
|
IP address version 6 recipient |
ipv6.dst \u003d\u003d 2001 :: 5 |
|
|
TCP Port Recipient or Sender |
||
|
TCP Port Recipient |
tCP.DSTPORT \u003d\u003d 80. |
|
|
TCP port of the sender |
tCP.Srcport \u003d\u003d 60234. |
|
|
UDP Port Recipient or Sender |
||
|
UDP Port Recipient |
udp.dstport \u003d\u003d 513. |
|
|
UDP port of the sender |
uDP.Srcport \u003d\u003d 40000. |
|
|
vtp.vlan_info.vlan_name. |
vtp.vlan_info.vlan_name \u003d\u003d Test |
|
|
bgp.originator_id |
BGP identifier (IPv4 address) |
bgp.originator_id \u003d\u003d 192.168.10.15 |
|
Next Hop BGP (IPv4 address) |
bGP.NEXT_HOP \u003d\u003d 192.168.10.15 |
|
|
RIP IPv4 Address |
rip.ip \u003d\u003d 200.0.2.0 |
|
|
OSPF router identifier |
ospf.advrouter \u003d\u003d 192.168.170.8. |
|
|
EIGRP autonomous system number |
||
|
Virtual IP address on the HSRP protocol |
hsrp.virt_ip \u003d\u003d 192.168.23.250 |
|
|
Virtual IP address by VRRP Protocol |
vrrp.ip_addr \u003d\u003d 192.168.23.250 |
|
|
Mac address sender or recipient Wi-Fi |
wLAN.ADDR \u003d\u003d 00: 1A: 6B: CE: FC: BB |
|
|
MAC address of the Wi-Fi Apiary |
wLAN.SA \u003d\u003d 00: 1A: 6B: CE: FC: BB |
|
|
MAC address of the recipient Wi-Fi |
wLAN.DA \u003d\u003d 00: 1A: 6B: CE: FC: BB |
And what filters most often use in your work?